Many fields of work have their own specific terminology. This is definitely true in cybersecurity. There’s a good amount of cybersecurity terms that are relevant in any type of organization, and often a big set of company specific acronyms to get to grips with as well. I can’t offer any help on those company specific terms, but I will share a lot here on Cyber Sherpas about some of the general cybersecurity terms that are among the most useful to know and understand.
Today’s example is Cyber Kill Chain.
The Cyber Kill Chain can be thought of as being derived from the military concept of a kill chain. I’m no expert on the military kill chain, but a little research on it suggests that it is focused on identifying a target, pulling forces together to attack the target, carrying out the attack and destroying the target. Now we see that cyber attack or cyber warfare capabilities are increasingly seen as part of kinetic / military warfare capabilities.
It was created by Lockheed Martin, who describe it like so:
Developed by Lockheed Martin, the Cyber Kill Chain® framework is part of the Intelligence Driven Defense® model for identification and prevention of cyber intrusions activity. The model identifies what the adversaries must complete in order to achieve their objective.
The seven steps of the Cyber Kill Chain® enhance visibility into an attack and enrich an analyst’s understanding of an adversary’s tactics, techniques and procedures.
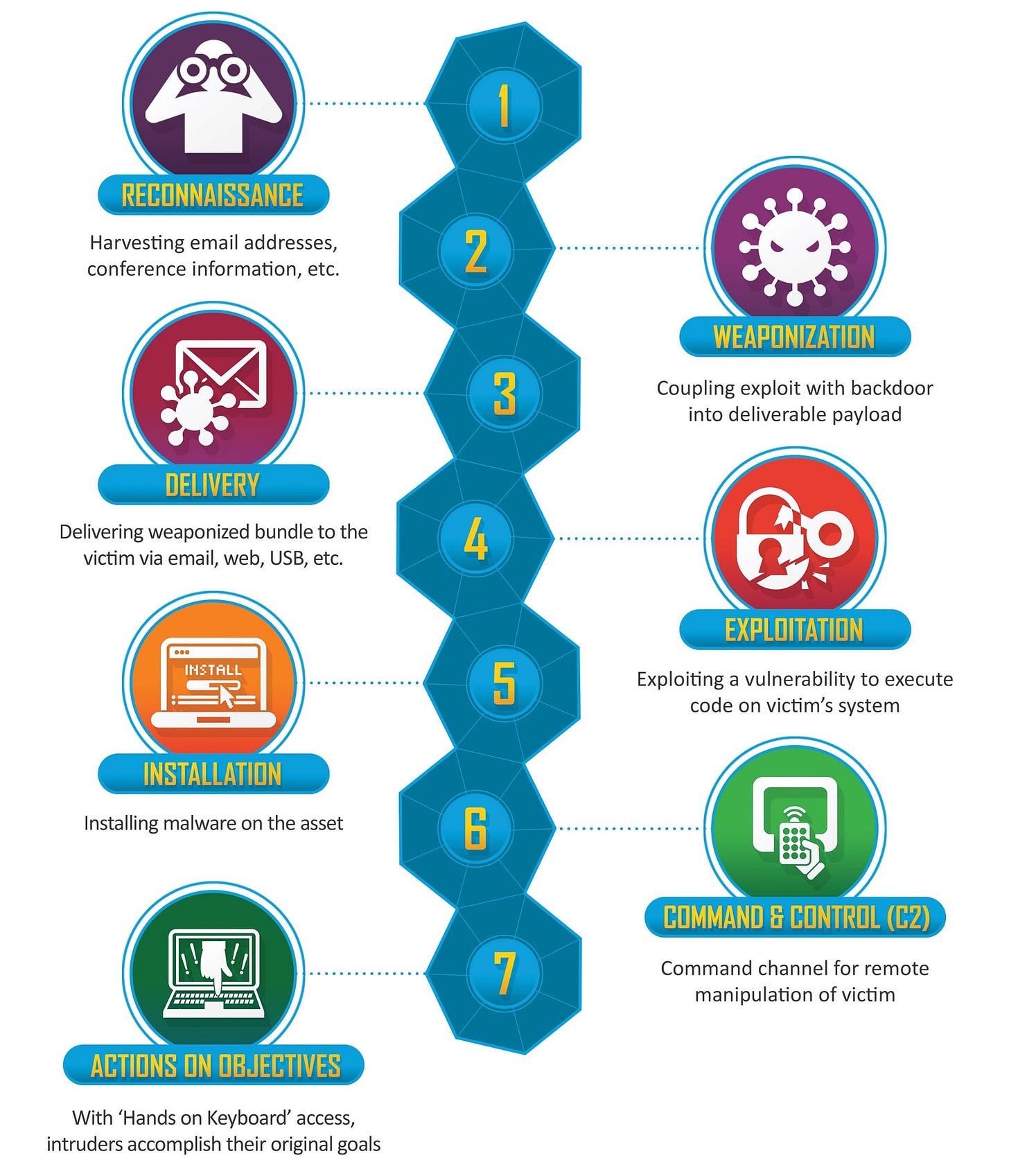
The infographic at the top of the post offers a clear outline of the Cyber Kill Chain.
Understanding The Cyber Kill Chain - and how we can detect its phases, respond to them, and if necessary recover from them - is a crucial element of cyber defenses. As shown in the Lockheed Martin graphic at the top of this post, The Cyber Kill Chain has 7 phases. Here’s a quick breakdown of what attackers are looking to do/achieve in each of the phases:
Reconnaissance: Gathering information on the targeted organization - on the people, processes, technologies, and vulnerabilities that can potentially be exploited in an attack.
Weaponization: Creating a new attack tool (e.g. malicious software) or modifying an existing tool to exploit any gaps or weaknesses identified in the reconnaissance phase.
Delivery: Deploying the attack tool in the target environment.Over recent years, this is most commonly done through phishing campaigns that lead a user to click on a link or open a malicious attachment. There are a number of other methods of course and attackers are continuously improving on these and developing new methods.
Exploitation: Triggered by the malicious software (malware) delivered in the previous phase, and leveraging weaknesses discovered earlier in the cyber kill chain, attackers can gather more information on the target environment they now have a foothold in and seek out additional vulnerabilities to exploit to achieve their goals.
Installation: Installing additional malware, privilege escalation (acquiring higher level permissions in order to be able to do more damage), and gaining access to more target systems and data.
Command and Control (or C2C): Establishing a communications channel from the target environment out to the attackers’ servers/environment. This channel can be used “inbound” for delivering more attack tools, and “outbound” to exfiltrate (take out, or steal) sensitive data from the target environment.
Actions on Objectives: This is the phase where impact occurs as part of or the ultimate goal of the attackers. This can include data exfiltration, loss of visibility (ability to monitor) key systems or processes, damage to systems that cause disruption to operations (or even a shutdown of operations), or destruction of critical devices or systems.
An offshoot of The Cyber Kill Chain is the Unified Kill Chain, developed by Paul Pols. I came across this while taking the excellent SANS SEC564 - Red Team Exercises & Adversary Emulation course. The Unified Kill Chain builds out a little on The Cyber Kill Chain and is another great resource for cyber defenders. As you can see below, this breaks down into three primary phases and their sub-phases. All of the phases in both the cyber kill chain models are useful in helping cyber defenders to understand the structure and stages of attacks and to review their current security controls and solutions and assess their ability to detect and defend at each phase/sub-phase of attacks.
Another theme that we’ll cover here at Cyber Sherpas is how AI - and specifiically generative AI (GenAI) is impacting cybersecurity. On that theme, this morning I asked Claude 4 to suggest some text for this post to make it even more targeted at people who are just trying to get into cybersecurity or who are mid career level. It offered a superb response, so I’ll share three parts of that here:
Real-World Context Example
The Target Breach Through the Kill Chain Lens
Let's see how this played out in the famous 2013 Target breach. Attackers started with reconnaissance on Target's vendors, identifying a smaller HVAC company with weaker security. They weaponized malware specifically for that vendor's systems, then delivered it via a phishing email. After exploiting the HVAC company's network, they installed additional tools to move laterally into Target's payment systems. Through command and control, they maintained persistent access for months. Finally, their actions on objectives resulted in stealing 40 million credit card numbers.
Notice how the attackers needed to succeed at every single phase. Target's defenders only needed to catch them at one stage to prevent or minimize the breach.
Why This Matters for Your Career
For SOC Analysts: You're the early warning system. Understanding which kill chain phase you're seeing helps prioritize alerts and guide your investigation steps.
For Incident Responders: The kill chain becomes your roadmap for understanding what happened, what might happen next, and where to focus containment efforts.
For Penetration Testers: You're literally following this playbook from the attacker's perspective, helping organizations identify where their defenses have gaps.
Interview Tip: Expect questions like "Walk me through how you'd investigate a potential breach" - the kill chain gives you a structured framework to demonstrate your thinking.
Quick Reference: Key Terms
Privilege Escalation: Getting higher-level access (like going from regular user to admin)
Exfiltration: The digital equivalent of stealing - moving data out of the target network
C2C (Command & Control): The attacker's "phone line" back to their systems
Lateral Movement: Spreading through a network after initial compromise
Detection Opportunities by Phase
A common theme in some cyber related discussions is along the lines of “the bad guys just need to find one vulnerability” to win. I prefer to embrace, and believe in, a more optimistic view on this. I want to cite where I first heard this optimistic view, but I will admit I am not 100 percent sure on this. I believe I first heard it via a presentation or conference talk by someone from Dragos, one of the world’s leading ICS Security firms.
The more optimistic view flips the equation, and says that as defenders we just need to detect the attackers at any stage (and hopefully and early stage) of their attack and have the right ability and playbooks in place to respond effectively and thwart the attack, or at least significantly reduce its impact.